 Facebook has announced that it’s teaming up with four of the world’s largest corporate data brokers to “enhance” the ad experience for users. Datalogix, Epsilon, Acxiom, and BlueKai obtain information gathered about users through online means (such as through cookies when users surf the web) as well as through offline means (such as through loyalty cards at supermarkets and product warranty cards).
Facebook has announced that it’s teaming up with four of the world’s largest corporate data brokers to “enhance” the ad experience for users. Datalogix, Epsilon, Acxiom, and BlueKai obtain information gathered about users through online means (such as through cookies when users surf the web) as well as through offline means (such as through loyalty cards at supermarkets and product warranty cards).
 After many years of professional consulting — serving stakeholders from the server room to the board room — I moved into management and encountered fresh perspective.
After many years of professional consulting — serving stakeholders from the server room to the board room — I moved into management and encountered fresh perspective.
I learned things that I wished someone had told me early in my career. I became a stakeholder and ate the proverbial dogfood. And along the way, I learned things that are worth sharing. I hope these “secrets” resonate with someone (as I believe they would have resonated with me 20 years ago).
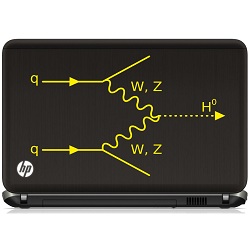 Scientists at the European Organization for Nuclear Research, known as CERN, announced yesterday that they’re even more certain than they were last summer (like, more than 99.999999999 percent sure) that they've seen a Higgs boson particle—even if it’s not the Higgs boson particle. Why does it even matter?
Scientists at the European Organization for Nuclear Research, known as CERN, announced yesterday that they’re even more certain than they were last summer (like, more than 99.999999999 percent sure) that they've seen a Higgs boson particle—even if it’s not the Higgs boson particle. Why does it even matter?
 Significant flaws in Microsoft Operating Systems and programs are becoming a smaller portion of the total. Secunia reports that 86 percent of active vulnerabilities in 2012 affected third-party products such as Java, Flash and Adobe Reader. In 2007, third-party vulnerabilities made up less than 60 percent of the total.
Significant flaws in Microsoft Operating Systems and programs are becoming a smaller portion of the total. Secunia reports that 86 percent of active vulnerabilities in 2012 affected third-party products such as Java, Flash and Adobe Reader. In 2007, third-party vulnerabilities made up less than 60 percent of the total.
 American voter support for same-sex marriage is inching up and now stands at 47 - 43 percent, including 54 - 38 percent among Catholic voters, according to a Quinnipiac University poll released today. Church leaders are out of touch with the views of Catholics in America today, all Catholics say 52 - 40 percent. Men say out of touch, 54 - 37 percent, while women agree by a smaller 49 - 43 percent margin.
American voter support for same-sex marriage is inching up and now stands at 47 - 43 percent, including 54 - 38 percent among Catholic voters, according to a Quinnipiac University poll released today. Church leaders are out of touch with the views of Catholics in America today, all Catholics say 52 - 40 percent. Men say out of touch, 54 - 37 percent, while women agree by a smaller 49 - 43 percent margin.
 "Tell no one, compromise everyone" -- Hackers exploit security vulnerabilities in software for 10 months on average before details of the holes surface in public, according to a new study based on a paper [PDF] on the research - Before We Knew It: An Empirical Study of Zero-Day Attacks In The Real World.
"Tell no one, compromise everyone" -- Hackers exploit security vulnerabilities in software for 10 months on average before details of the holes surface in public, according to a new study based on a paper [PDF] on the research - Before We Knew It: An Empirical Study of Zero-Day Attacks In The Real World.
 John Leyden at The Register reports that security experts uncovered privacy concerns in mobile applications available from both the Barack Obama and Mitt Romney presidential campaigns. Researchers at GFI Software examined the Android versions of both products and are alarmed at the invasive nature of the offerings.
John Leyden at The Register reports that security experts uncovered privacy concerns in mobile applications available from both the Barack Obama and Mitt Romney presidential campaigns. Researchers at GFI Software examined the Android versions of both products and are alarmed at the invasive nature of the offerings.
Obama for America and Mitt’s VP request permissions, access to services and data and demonstrate capabilities beyond product expectations. Each of the apps cross-posts on users' behalf and report back to base.
 The next time you feel the need to reach out, touch base, shift a paradigm, leverage a best practice or join a tiger team, by all means do it. Just don’t say you’re doing it.
The next time you feel the need to reach out, touch base, shift a paradigm, leverage a best practice or join a tiger team, by all means do it. Just don’t say you’re doing it.
People use jargon as a substitute for thinking hard and clearly about their goals and the direction they wish to give others. Jargon masks meaning. Jargon can mean different things to different people. You might be saying one thing -- while your audience is hearing another.
 A highly sophisticated computer virus is infecting computers in Middle Eastern and North African countries. It appears to have been at least five years ago. Is this state-sponsored cyber espionage?
A highly sophisticated computer virus is infecting computers in Middle Eastern and North African countries. It appears to have been at least five years ago. Is this state-sponsored cyber espionage?
Kaspersky Lab, a Russian cyber-security software maker, said it discovered the virus, dubbed Flame, after a U.N. telecommunications agency asked it to analyze data on malicious software across the Middle East in search of the data-wiping virus reported by Iran.
 Yahoo released its Axis extension for Chrome and accidentally leaked its private security key that could allow anyone to create malicious plugins masquerading as official Yahoo software. The result is that a miscreant could forge malicious software to run amok on unsuspecting victim computers and it would appear to be coming from Yahoo.
Yahoo released its Axis extension for Chrome and accidentally leaked its private security key that could allow anyone to create malicious plugins masquerading as official Yahoo software. The result is that a miscreant could forge malicious software to run amok on unsuspecting victim computers and it would appear to be coming from Yahoo.
An Australian researcher exposed the certificate mistake, and said users should not install the extension "until the issue is clarified." He examined the extension’s source code and found the private certificate, which Yahoo uses to sign the application to prove it is genuine and unaltered.

Do you know an ogre? Are you an ogre?
Ogres can exist at any level in an organization.
Ogres come from many backgrounds and can be any color, gender, belief system, or orientation. But ogres are easy to spot. What gives them away? Perhaps, it is the Ogres' lack of etiquette in the office place. Or is it the ogres' dysfunctional (or broken) ethical compass. Whether you are an Ogre or the victim of an Ogre, there are five Ogre specific disruptors of performance you should look out for that will negatively affect you and your stakeholders...
 A new variant of SpyEye malware allows cybercriminals to monitor potential bank fraud victims by hijacking their Web cams and microphones, according to security researchers from Kaspersky Lab May 21. SpyEye is a computer trojan that specifically targets online banking users.
A new variant of SpyEye malware allows cybercriminals to monitor potential bank fraud victims by hijacking their Web cams and microphones, according to security researchers from Kaspersky Lab May 21. SpyEye is a computer trojan that specifically targets online banking users.
Like its older cousin, Zeus, SpyEye is no longer being developed by its original author but is still widely used by cybercriminals. SpyEye’s plug-in-based architecture allows third-party malware developers to extend its original functionality, a Kaspersky Lab malware researcher said.
 A NASA spokesperson told SecurityWeek they were investigating claims made by a group of Iranian hackers May 16 that they have compromised the SSL certificate used on the NASA Solicitation and Proposal Integrated Review and Evaluation System (NSPIRES) Web site.
A NASA spokesperson told SecurityWeek they were investigating claims made by a group of Iranian hackers May 16 that they have compromised the SSL certificate used on the NASA Solicitation and Proposal Integrated Review and Evaluation System (NSPIRES) Web site.
The Iranian student group comprised of programmers and hackers — known as the Cyber Warriors Team — claimed to have compromised the SSL cert was compromised by exploiting an existing vulnerability within the portal’s log-in system.
 Researchers from Kapersky Lab recently reported on a new distributed denial-of-service (DDoS) tool. The HTTP Unbearable Load King (HULK) tool is different from others of its kind in that it does not simply hit a server with a massive load of TCP SYN requests or other predictable packets. HULK generates numerous unique requests designed to prevent server defenses from recognizing a pattern and filtering the attack traffic. The HULK DDoS tool is the work of Barry Shteiman, a security pro who developed it out of frustration with the obvious patterns produced by other such tools.
Researchers from Kapersky Lab recently reported on a new distributed denial-of-service (DDoS) tool. The HTTP Unbearable Load King (HULK) tool is different from others of its kind in that it does not simply hit a server with a massive load of TCP SYN requests or other predictable packets. HULK generates numerous unique requests designed to prevent server defenses from recognizing a pattern and filtering the attack traffic. The HULK DDoS tool is the work of Barry Shteiman, a security pro who developed it out of frustration with the obvious patterns produced by other such tools.
 Security experts found many compromised WordPress and Joomla Web sites used by spammers to advertise sketchy diet pills and counterfeit luxury goods. The owners of these sites are most likely unaware of what is going on. Web masters often fail to check their sites’ subdirectories for signs of malicious files and Web pages, thus allowing cybercriminals to use the domain’s reputation to host their scams. Attackers often brute-force administrator passwords to gain access to a site’s back end.
Security experts found many compromised WordPress and Joomla Web sites used by spammers to advertise sketchy diet pills and counterfeit luxury goods. The owners of these sites are most likely unaware of what is going on. Web masters often fail to check their sites’ subdirectories for signs of malicious files and Web pages, thus allowing cybercriminals to use the domain’s reputation to host their scams. Attackers often brute-force administrator passwords to gain access to a site’s back end.
 Operators of America’s power, water, and manufacturing facilities use industrial control systems (ICS) to manage them. However, the security of these systems, increasingly linked with Microsoft Windows and the Internet, is now under intense scrutiny because of growing awareness that they could be attacked and cause massive disruptions.
Operators of America’s power, water, and manufacturing facilities use industrial control systems (ICS) to manage them. However, the security of these systems, increasingly linked with Microsoft Windows and the Internet, is now under intense scrutiny because of growing awareness that they could be attacked and cause massive disruptions.
- Chief Legal Officers and CIOs Must Work Together
- Rinzai Zen - Fujaku, Fugu
- Hacking Governments With Hijacked Sites
- Social Engineers Target Utilities
- Steam Cracker Steals User Credentials
- Wearable Firewall Stops Pacemaker Hacking
- Human Body Vulnerable to Cyberattack
- Former Intel Employee Pleads Guilty
- 10-Minute Executive Brief
- US Utilities Under Daily Cyber-attack






