
3pm -- I’ve slept with a CPAP for nearly a third of my life.
From the beginning, my CPAP has improved my sleep. I sleep with less disturbance and awaken refreshed. I adapted to it easily, largely, because I never needed a full face mask. The design of a nasal-pillow mask is such that I can still read in bed before going to sleep and I can lie on either side without discomfort. Head congestion; however, is an unpleasant additional challenge. The positive air pressure helps but has clear limits. As I suffocate, my body tries to compensate. I either open my mouth to take a breath or I suddenly wake up gasping. Neither is pleasant.

 2pm -- “Another day...”, I say to with a sigh to no one in particular.
2pm -- “Another day...”, I say to with a sigh to no one in particular. Today, there is a visceral sense of relief that is being felt by many Americans. The rousing performance by Joe Biden in the Super Tuesday primary represents the extraordinary angst many people have for the possibility of a Bernie Sanders presidency. A “feelings” trend appears to have emerged that has surprised quite a few people, including many that are completely comfortable with Democratic Socialism. The feeling is rooted in the fear and dread of a second-term Donald Trump presidency.
Today, there is a visceral sense of relief that is being felt by many Americans. The rousing performance by Joe Biden in the Super Tuesday primary represents the extraordinary angst many people have for the possibility of a Bernie Sanders presidency. A “feelings” trend appears to have emerged that has surprised quite a few people, including many that are completely comfortable with Democratic Socialism. The feeling is rooted in the fear and dread of a second-term Donald Trump presidency. Massive amounts of fake news and conspiratorial content have spread over social media before and after the 2016 US Presidential Elections despite intense fact-checking efforts.
Massive amounts of fake news and conspiratorial content have spread over social media before and after the 2016 US Presidential Elections despite intense fact-checking efforts. Research indicates that smart phones are
Research indicates that smart phones are  Science is an endeavour that draws on all of our uniquely human abilities. The need of science appeals to and is guided by common values. Therefore, it needs feelings and imagination as much as observation, analysis and logic. However, here’s a view of science you might recognise as common, or at least see promoted:
Science is an endeavour that draws on all of our uniquely human abilities. The need of science appeals to and is guided by common values. Therefore, it needs feelings and imagination as much as observation, analysis and logic. However, here’s a view of science you might recognise as common, or at least see promoted: In a newly released strategy, the United States has proposed an increased global effort to locate 300,000 or so Earth-impact risks and prepare for potential future meteor collisions that could destroy cities, civilization, or all life as we know it. Near Earth Objects (NEOs) are defined as asteroids or comets that come near our planet’s orbit.
In a newly released strategy, the United States has proposed an increased global effort to locate 300,000 or so Earth-impact risks and prepare for potential future meteor collisions that could destroy cities, civilization, or all life as we know it. Near Earth Objects (NEOs) are defined as asteroids or comets that come near our planet’s orbit. In general, we feel awe when in the presence of something that is so big, beautiful, powerful or complex that it is hard to wrap our heads around (e.g. gazing at the stars and contemplating the vastness of the universe, witnessing the destructive force of a natural disaster). We feel it when we are struck dumb by the presence of the mysterious, magical, wondrous or beautiful and its experience drives us to seek explanations. Something has not only defied our expectations about how the world works, but it has made us want to understand, explain and find meaning in what has happened.
In general, we feel awe when in the presence of something that is so big, beautiful, powerful or complex that it is hard to wrap our heads around (e.g. gazing at the stars and contemplating the vastness of the universe, witnessing the destructive force of a natural disaster). We feel it when we are struck dumb by the presence of the mysterious, magical, wondrous or beautiful and its experience drives us to seek explanations. Something has not only defied our expectations about how the world works, but it has made us want to understand, explain and find meaning in what has happened. Most of us have experienced this creeping sense of being overwhelmed: the feeling not merely that our lives are full of activity – that can be exhilarating – but that time is slipping out of our control. The quest for increased personal productivity – for making the best possible use of your limited time – is a dominant motif of our age. And yet the truth is that more often than not, techniques designed to enhance one’s personal productivity seem to exacerbate the very anxieties they were meant to allay. The better you get at managing time, the less of it you feel that you have. It’s understandable that we respond to the ratcheting demands of modern life by trying to make ourselves more efficient. But what if all this efficiency just makes things worse?
Most of us have experienced this creeping sense of being overwhelmed: the feeling not merely that our lives are full of activity – that can be exhilarating – but that time is slipping out of our control. The quest for increased personal productivity – for making the best possible use of your limited time – is a dominant motif of our age. And yet the truth is that more often than not, techniques designed to enhance one’s personal productivity seem to exacerbate the very anxieties they were meant to allay. The better you get at managing time, the less of it you feel that you have. It’s understandable that we respond to the ratcheting demands of modern life by trying to make ourselves more efficient. But what if all this efficiency just makes things worse? A liver hormone called FGF21 may regulate alcohol drinking by acting directly on a receptor in the brain, according to a new study. This raises the possibility of a new therapeutic pathway that could one day be targeted to reduce the desire for alcohol in problem drinkers. The new study, by researchers from Imperial College London, King’s College London, and UT Southwestern Medical Center, for the first time highlights a liver-brain axis which plays an important role in regulating the consumption of alcohol.
A liver hormone called FGF21 may regulate alcohol drinking by acting directly on a receptor in the brain, according to a new study. This raises the possibility of a new therapeutic pathway that could one day be targeted to reduce the desire for alcohol in problem drinkers. The new study, by researchers from Imperial College London, King’s College London, and UT Southwestern Medical Center, for the first time highlights a liver-brain axis which plays an important role in regulating the consumption of alcohol. A large enough solar flare could knock out electrical grids we have come to rely on for day-to-day life. On 13 October 2016, President Barack Obama issued an
A large enough solar flare could knock out electrical grids we have come to rely on for day-to-day life. On 13 October 2016, President Barack Obama issued an  When Dr. Harry Selker was working as a cardiologist in the 1970s, clot-busting drugs were showing great promise against heart attacks. One medical treatment Selker is researching is a cocktail of glucose, insulin and potassium, known by its chemical initials GIK. More than 50 years ago, studies with baboons and rabbits indicated that GIK appeared to actually prevent heart attacks. The simple concoction protected heart muscles against damage. Selker says: "So it was very encouraging. It was extraordinary, really."
When Dr. Harry Selker was working as a cardiologist in the 1970s, clot-busting drugs were showing great promise against heart attacks. One medical treatment Selker is researching is a cocktail of glucose, insulin and potassium, known by its chemical initials GIK. More than 50 years ago, studies with baboons and rabbits indicated that GIK appeared to actually prevent heart attacks. The simple concoction protected heart muscles against damage. Selker says: "So it was very encouraging. It was extraordinary, really." The admonition given by the Buddha in the first verse of the Dhammapada that the human mind is responsible for everything we do -- good or evil, is reiterated and embodied in the preamble to the UNESCO Charter of Human Rights which states: 'Since wars begin in the minds of men, it is in the minds of men that the defense of peace must be constructed.'
The admonition given by the Buddha in the first verse of the Dhammapada that the human mind is responsible for everything we do -- good or evil, is reiterated and embodied in the preamble to the UNESCO Charter of Human Rights which states: 'Since wars begin in the minds of men, it is in the minds of men that the defense of peace must be constructed.' Do you know someone who needs hours alone every day? Who loves conversations about their ideas or feelings, and can give a dynamite presentation to a big audience, but often seems awkward in groups and maladroit at small talk? Who has to be dragged to parties and then needs the rest of the day to recuperate? Who growls or scowls or grunts or winces when accosted with pleasantries by people who are just trying to be nice? If so, do you redouble your efforts to draw him out? Regard him as aloof, arrogant, rude? Tell this person he is "too serious," or ask if he is okay?
Do you know someone who needs hours alone every day? Who loves conversations about their ideas or feelings, and can give a dynamite presentation to a big audience, but often seems awkward in groups and maladroit at small talk? Who has to be dragged to parties and then needs the rest of the day to recuperate? Who growls or scowls or grunts or winces when accosted with pleasantries by people who are just trying to be nice? If so, do you redouble your efforts to draw him out? Regard him as aloof, arrogant, rude? Tell this person he is "too serious," or ask if he is okay?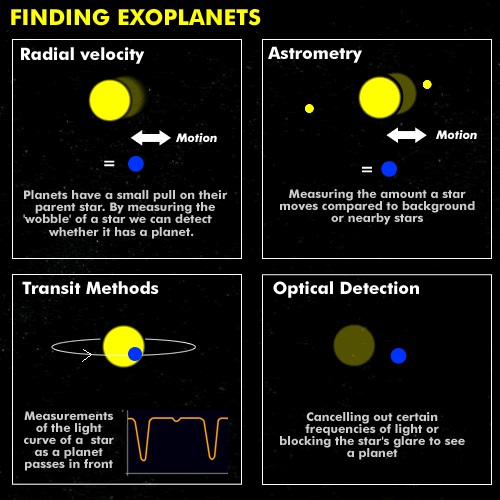 This week astronomers using NASA’s Kepler space telescope announced that the planet-hunting spacecraft had increased its catalogue by an additional 1,284 worlds. This is the greatest number of planets ever announced at one time. A paper summarizing the findings appears in The Astrophysical Journal. The total exoplanet tally now stands at about 3,200, and Kepler has found 2,235 of them, NASA officials said.
This week astronomers using NASA’s Kepler space telescope announced that the planet-hunting spacecraft had increased its catalogue by an additional 1,284 worlds. This is the greatest number of planets ever announced at one time. A paper summarizing the findings appears in The Astrophysical Journal. The total exoplanet tally now stands at about 3,200, and Kepler has found 2,235 of them, NASA officials said. Scientists have created an “atlas of the brain” that reveals how the meanings of words are arranged across different regions of the organ. Like a colourful quilt laid over the cortex, the atlas displays in rainbow hues how individual words and the concepts they convey can be grouped together in clumps of white matter. “Our goal was to build a giant atlas that shows how one specific aspect of language is represented in the brain, in this case semantics, or the meanings of words,” said Jack Gallant, a neuroscientist at the University of California, Berkeley.
Scientists have created an “atlas of the brain” that reveals how the meanings of words are arranged across different regions of the organ. Like a colourful quilt laid over the cortex, the atlas displays in rainbow hues how individual words and the concepts they convey can be grouped together in clumps of white matter. “Our goal was to build a giant atlas that shows how one specific aspect of language is represented in the brain, in this case semantics, or the meanings of words,” said Jack Gallant, a neuroscientist at the University of California, Berkeley.




