 Buddhist monks from around the world gathered at Thailand's ancient Ayutthaya city on Thursday for the last day of the International Buddhist Confederation (IBC) during which they laid emphasis on actions to tackle climate change.
Buddhist monks from around the world gathered at Thailand's ancient Ayutthaya city on Thursday for the last day of the International Buddhist Confederation (IBC) during which they laid emphasis on actions to tackle climate change.
The delegates from 320 organisations in 39 countries, including the United States, the United Kingdom, Germany, Mexico and Brazil, participated in the second gathering of the IBC. One of the key issues discussed were how the monks in different countries find ways to address the climate change.


 David Bowie has died after a battle with cancer, his rep confirmed to Billboard. He was 69. "David Bowie died peacefully today surrounded by his family after a courageous 18 month battle with cancer. While many of you will share in this loss, we ask that you respect the family’s privacy during their time of grief," read a statement posted on the artist's official social media accounts.
David Bowie has died after a battle with cancer, his rep confirmed to Billboard. He was 69. "David Bowie died peacefully today surrounded by his family after a courageous 18 month battle with cancer. While many of you will share in this loss, we ask that you respect the family’s privacy during their time of grief," read a statement posted on the artist's official social media accounts.  The Iranian foreign minister on Monday reacted to an open letter to Iran’s leaders by 47 U.S. Republican senators who had warned Tehran that any nuclear deal that the Islamic Republic signs with President Barack Obama’s administration won’t last after Obama leaves office. Mohammad Javad Zarif said the letter lacks “legal validity” and shows that the signatories of the letter are “ignorant of international law”. “In our view this letter has no legal validity and is just a propaganda scheme,” Zarif noted. The letter proved that “like” Israeli Prime Minister Benjamin Netanyahu these senators “are opposed to any deal”.
The Iranian foreign minister on Monday reacted to an open letter to Iran’s leaders by 47 U.S. Republican senators who had warned Tehran that any nuclear deal that the Islamic Republic signs with President Barack Obama’s administration won’t last after Obama leaves office. Mohammad Javad Zarif said the letter lacks “legal validity” and shows that the signatories of the letter are “ignorant of international law”. “In our view this letter has no legal validity and is just a propaganda scheme,” Zarif noted. The letter proved that “like” Israeli Prime Minister Benjamin Netanyahu these senators “are opposed to any deal”. At the time that the ruling was delivered, Kennedy’s faith that access and influence would not corrupt the system was exceeded in curiousness only by his belief that the American people would feel similarly. But as the years have passed, and as studies showing the U.S. to be a donor-run system akin to oligarchy have gone mainstream, his declaration has begun to make a bit more sense. Just so long as “the electorate” is defined as the lobbying industry and its clients, his prediction looks downright clairvoyant.
At the time that the ruling was delivered, Kennedy’s faith that access and influence would not corrupt the system was exceeded in curiousness only by his belief that the American people would feel similarly. But as the years have passed, and as studies showing the U.S. to be a donor-run system akin to oligarchy have gone mainstream, his declaration has begun to make a bit more sense. Just so long as “the electorate” is defined as the lobbying industry and its clients, his prediction looks downright clairvoyant. Successful companies frequently rely heavily on just one product for the majority of their sales and profit. Because each product represents such an outsized share of their respective company’s revenue, the products’ tremendous margins are the foundation of the company’s profit.
Successful companies frequently rely heavily on just one product for the majority of their sales and profit. Because each product represents such an outsized share of their respective company’s revenue, the products’ tremendous margins are the foundation of the company’s profit.  Facebook has announced that it’s teaming up with four of the world’s largest corporate data brokers to “enhance” the ad experience for users. Datalogix, Epsilon, Acxiom, and BlueKai obtain information gathered about users through online means (such as through cookies when users surf the web) as well as through offline means (such as through loyalty cards at supermarkets and product warranty cards).
Facebook has announced that it’s teaming up with four of the world’s largest corporate data brokers to “enhance” the ad experience for users. Datalogix, Epsilon, Acxiom, and BlueKai obtain information gathered about users through online means (such as through cookies when users surf the web) as well as through offline means (such as through loyalty cards at supermarkets and product warranty cards). After many years of professional consulting — serving stakeholders from the server room to the board room — I moved into management and encountered fresh perspective.
After many years of professional consulting — serving stakeholders from the server room to the board room — I moved into management and encountered fresh perspective.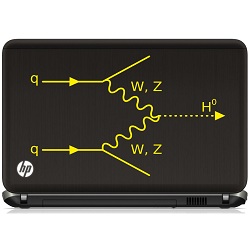 Scientists at the European Organization for Nuclear Research, known as CERN, announced yesterday that they’re even more certain than they were last summer (like, more than 99.999999999 percent sure) that they've seen a Higgs boson particle—even if it’s not the Higgs boson particle. Why does it even matter?
Scientists at the European Organization for Nuclear Research, known as CERN, announced yesterday that they’re even more certain than they were last summer (like, more than 99.999999999 percent sure) that they've seen a Higgs boson particle—even if it’s not the Higgs boson particle. Why does it even matter? Significant flaws in Microsoft Operating Systems and programs are becoming a smaller portion of the total.
Significant flaws in Microsoft Operating Systems and programs are becoming a smaller portion of the total.  American voter support for same-sex marriage is inching up and now stands at 47 - 43 percent, including 54 - 38 percent among Catholic voters, according to a Quinnipiac University poll released today. Church leaders are out of touch with the views of Catholics in America today, all Catholics say 52 - 40 percent. Men say out of touch, 54 - 37 percent, while women agree by a smaller 49 - 43 percent margin.
American voter support for same-sex marriage is inching up and now stands at 47 - 43 percent, including 54 - 38 percent among Catholic voters, according to a Quinnipiac University poll released today. Church leaders are out of touch with the views of Catholics in America today, all Catholics say 52 - 40 percent. Men say out of touch, 54 - 37 percent, while women agree by a smaller 49 - 43 percent margin.  "Tell no one, compromise everyone" -- Hackers exploit security vulnerabilities in software for 10 months on average before details of the holes surface in public, according to a new study based on a
"Tell no one, compromise everyone" -- Hackers exploit security vulnerabilities in software for 10 months on average before details of the holes surface in public, according to a new study based on a  John Leyden
John Leyden The next time you feel the need to reach out, touch base, shift a paradigm, leverage a best practice or join a tiger team, by all means do it. Just don’t say you’re doing it.
The next time you feel the need to reach out, touch base, shift a paradigm, leverage a best practice or join a tiger team, by all means do it. Just don’t say you’re doing it. A highly sophisticated computer virus is infecting computers in Middle Eastern and North African countries. It appears to have been at least five years ago. Is this state-sponsored cyber espionage?
A highly sophisticated computer virus is infecting computers in Middle Eastern and North African countries. It appears to have been at least five years ago. Is this state-sponsored cyber espionage? Yahoo released its Axis extension for Chrome and accidentally leaked its private security key that could allow anyone to create malicious plugins masquerading as official Yahoo software. The result is that a miscreant could forge malicious software to run amok on unsuspecting victim computers and it would appear to be coming from Yahoo.
Yahoo released its Axis extension for Chrome and accidentally leaked its private security key that could allow anyone to create malicious plugins masquerading as official Yahoo software. The result is that a miscreant could forge malicious software to run amok on unsuspecting victim computers and it would appear to be coming from Yahoo.




